This is the first in a new series of Secret blog posts that will cover dApps that are utilizing Secret Network’s Privacy as a Service capability.
Earlier this month we announced Privacy as a Service (PaaS) – Secret Network’s ability to provide private computation to other blockchain networks. This is achieved through the use of cross-chain communication protocols. Inter Blockchain Communication (IBC) and Axelar General Message Passing (GMP) are some examples of popular protocols in use today, but PaaS is not limited to just these!
Today, we’re taking a look at a dApp that has built its own custom cross-chain communication solution, enabling it to operate on Polygon while managing encrypted data on Secret!
Introducing BIDSHOP
BIDSHOP is a gamified and privatized auction house for NFTs and DeFi, with the purpose of providing new ways to generate liquidity for all web3 assets. It provides a variety of auction products that can be used by either blockchain projects or individuals. Some examples include:
- Initial Bid Offering: Derived from the “highest unique offer auction” mechanism, bidders compete to win either non-fungible or fungible underlying assets while only paying small fees for each bid placed.
- Silent NFT Auctions: Sellers choose a secret minimum price, and buyers compete in a closed auction. The result: The highest possible price for in-demand assets.
- Fair NFT Mint Auction: Launch an NFT Mint at true market valuation while bootstrapping the future holders community. Allow future holders to determine the true fair mint value via a novel secret bidding mechanism. Incentivize bidders who bid as close as possible to the final mint price determined.
- Fair Launch IDO Auction: Similar to the Fair NFT mint, Launch your fungible token at the fairest possible price while bootstrapping your future token holders community. This auction also helps fight pumped IDO’s and provided anti-bot protection.
- Debt Auction: Sell DeFi debt positions to anyone with competitive pricing on the IOUs.
All of these auction products make use of a similar data model – users place bids, which are encrypted and not revealed to other users, allowing for novel, gamified auctions.
Technical Architecture
At a high-level, BIDSHOP consists of three primary components:
- Polygon Network: Hosts the smart contracts for rewards distribution, bid fee management, and other non-private aspects.
- Secret Network: Used for the encryption of bids, ensuring a secure and private bidding process.
- Custom Communication Layer: Facilitates secure data exchange between the Polygon and Secret Network contracts, ensuring seamless interaction between the two networks.
Auction Flow
BIDSHOP follows a well-defined sequence of steps to ensure secure, private, and fair gameplay. Below is the outline of the game’s auction flow:
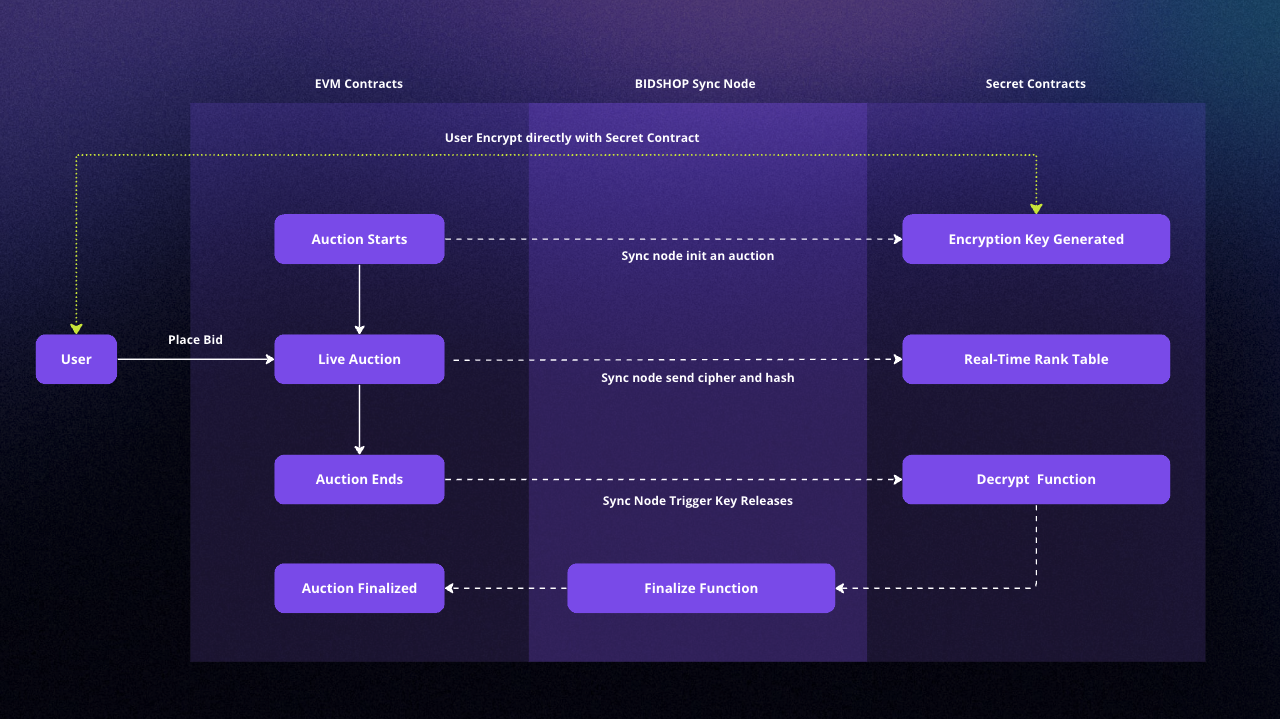
- Encryption Key Generation: An encryption key is generated within a secure enclave on Secret Network. This encryption function is available for all users to encrypt their bids but cannot be used to decrypt them.
- Bid Encryption: Users place bids by encrypting their bid amounts directly against the encryption function with the secret contract. This process does not reveal the bid amounts to anyone, ensuring confidentiality.
- Cipher and Hash Transaction: The encrypted bids (ciphers) and their corresponding hashes are submitted to the EVM contract hosted on the Polygon network.
- Rank Table Generation: The communication layer feeds the ciphers to Secret Network, which generates a real-time rank table based on the encrypted bids.
- Auction Ends: The auction concludes after a predetermined period. No new bids can be placed or processed after this point.
- Key Release: The communication layer releases the encryption key, allowing all parties to decrypt the bids. This process is facilitated only after the auction ends, ensuring fair gameplay.
- Finalization: The communication layer feeds the decrypted bid amounts to the EVM contract on the Polygon network for finalization and reward distribution.
By following this sequence, BIDSHOP’s technology ensures a secure, private, and fair bidding environment that provides an engaging user experience while preserving the integrity of the game.
Encryption Algorithm
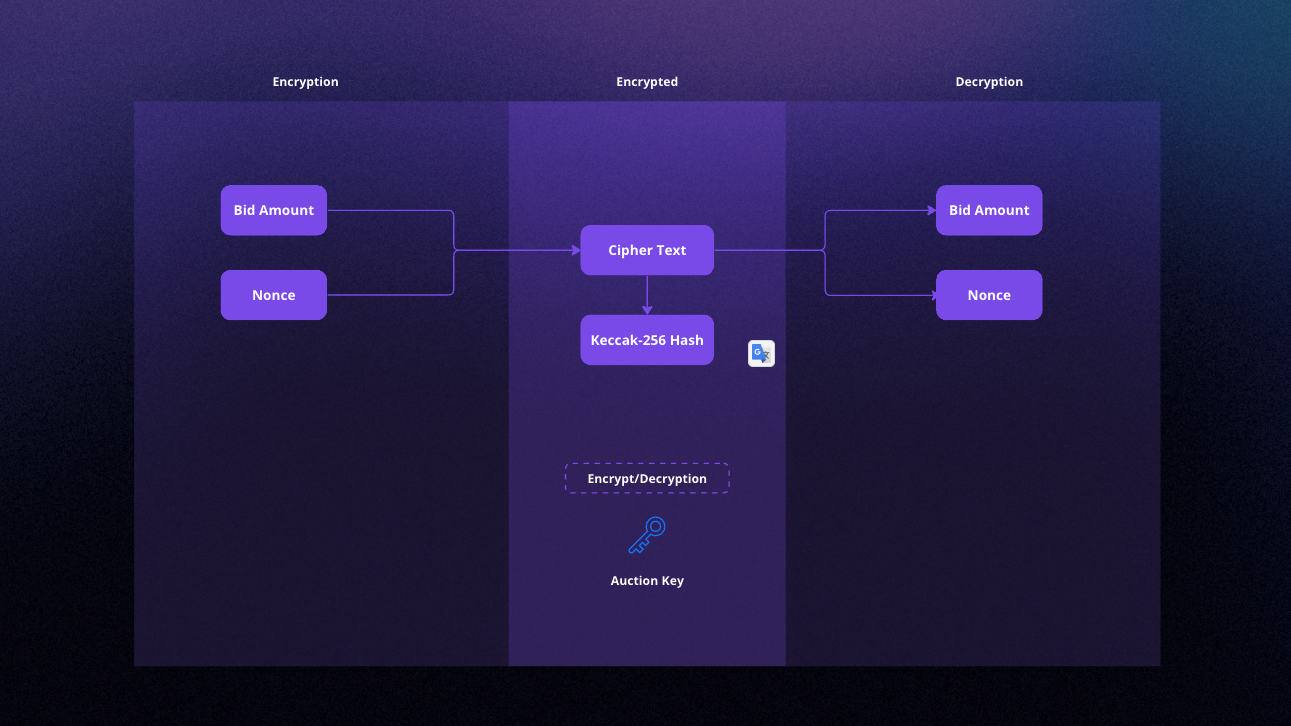
To ensure a high level of security, BIDSHOP uses the XChaCha20 encryption algorithm, and a random nonce is generated each time a user bids. This approach helps protect the confidentiality of bid amounts while maintaining the integrity of the game. The auction key and nonce, used for encrypting bids with XChaCha20, are randomly created for every auction. The custom communication layer can only reveal these values during the auction. Importantly, the smart contract on Secret Network includes a time check condition that prevents the custom communication layer from revealing the bid amounts before the auction’s end time. This mechanism ensures that the bid amounts remain private and secure throughout the auction process, and only the necessary information is revealed when required.
Why BIDSHOP chose Secret
Secret is unique because it uses symmetric and asymmetric encryption protocols, ensuring robust security and privacy. Asymmetric cryptography achieves consensus and shares secrets between nodes and users, while symmetric cryptography is used for input/output encryption with users of Secret Contracts and internal contract state encryption. This approach effectively maintains the confidentiality of users’ bids until the end of the auction and protects sensitive information.
BIDSHOP’s fairness is achieved through Secret Network’s ability to enforce critical conditions in smart contracts, such as making the encryption key available only after the auction ends. As a result, this guarantees every participant an equal and fair chance of winning the auction.
While preserving privacy, Secret Network also provides the necessary transparency for BIDSHOP. Users can verify the legitimacy of the auction process and the custom communication layer’s reliability through the provided verification instructions.
Fairness and Verification of Auctions
Ensuring the fairness of an auction is integral to BIDSHOP’s value proposition. Below, we outline the mechanisms and steps involved in proving that an auction was conducted fairly:
- Encryption Source Declaration: A secret contract is declared the encryption source for all auctions.
- Key Allocation: Each auction is allocated a dedicated encryption key.
- Hash Generation: Hashes are generated from a bid amount and a nonce. When the ciphers are revealed, the bid amount and nonce must match their corresponding hash.
The integrity of the custom communication layer can be verified retroactively. It can be exposed at any time if it is found to have provided false information. The steps to verify a finalized round are as follows:
- Fetch all fed bid hashes and ciphers of a round (e.g., with SubGraph).
- Decrypt all the ciphers using the designated auction ID in the secret contract.
- Fetch all the bid values from the EVM contract hosted on the Polygon network.
- The decrypted bid amounts should match the amounts in the EVM contract, given that the nonce and bid amount from a cipher match. If a cipher of an auction is decryptable via its designated key, but the bid amount is not present in the EVM contract, the custom communication layer is proven guilty.
Additional checks for the legitimacy of the custom communication layer include:
- Each auction should have the same number of bids on the EVM and Secret Network, excluding bids with invalid ciphers.
- The release of the encryption key should always occur after the final block of the auction has been executed.
These mechanisms and verification steps ensure the fairness and reliability of the cross-chain auction game, providing users with confidence in the integrity of the process.
Upcoming Launch Events
BIDSHOP will be launching the BIDS token today, June 29th, which will be required for bidding on the platform. Soon afterward on July 2nd, the first auction will take place. Initially, the BIDSHOP platform will be permissioned and all auctions will pre-approved and hosted by the team. In a later phase, auction creation will be opened to the public, allowing anyone to make use of their line of auction products.
To keep up with what BIDSHOP has going on, join their Discord, Telegram, and follow them on Twitter!
What’s Next for Privacy as a Service?
BIDSHOP is an excellent example of just how flexible and powerful Secret’s Privacy as a Service capabilities are. Existing cross-chain protocols like IBC currently enable Secret to communicate with Cosmos SDK-based blockchains, and Axelar GMP will soon enable Secret to communicate with EVM-based blockchains. However, developers can also build new cross-chain communication protocols to bring PaaS to other ecosystems. In fact, several new solutions are in development right now! One such example is Centauri, a blockchain connecting the Polkadot ecosystem to Cosmos via IBC.
Today marks a major step in connecting @Polkadot and @cosmos, as @ComposableFin has launched Centauri beta!
As more ecosystems connect to IBC, Secret’s Privacy as a Service capabilities continue to expand. Look forward to integrations with Polkadot dApps!https://t.co/X2asEWdYV0
— 𝕊ecret Network 🤫⚡️ (@SecretNetwork) June 29, 2023
If you’re a developer interested in utilizing Privacy as a Service, check out the Secret Network Developer Documentation for design ideas and code examples. You can also get help from our developer community on Discord or Telegram. If you’re looking for more direct support, contact the Secret Network team and we’ll discuss ways that Secret can support your PaaS project, including technical guidance, funding, and marketing.
Onwards and Upwards


