Explorer update coming August 1st! Mintscan is being retired. Check out
and

Confidential Computing Layer
Secret Network brings decentralized confidential computing (DeCC) to Web3, enabling dApps to leverage encrypted data. Compatible with EVM, Cosmos SDK, and Solana, Secret’s Confidential Computing Layer unlocks innovative use cases for your applications.
Decentralized confidential computing

Confidential Computing Layer
Secret Network brings decentralized confidential computing (DeCC) to Web3, enabling dApps to leverage encrypted data. Compatible with EVM, Cosmos SDK, and Solana, Secret’s Confidential Computing Layer unlocks innovative use cases for your applications.
Decentralized confidential computing

Confidential Computing Layer
Secret Network brings decentralized confidential computing (DeCC) to Web3, enabling dApps to leverage encrypted data. Compatible with EVM, Cosmos SDK, and Solana, Secret’s Confidential Computing Layer unlocks innovative use cases for your applications.
Decentralized confidential computing
Available on
Use case
Discover what’s possible
Use case
Discover what’s possible
Use case
Discover what’s possible
Use case
Discover what’s possible
Use case
Discover what’s possible
Use case
Discover what’s possible
Seamless UX
Build your dApp on your preferred blockchain, while Secret handles the confidential computation on the backend. Your users can use their usual wallet, while still benefiting from Secret's capabilities.
Highly Interoperable
Utilizing SecretPath, IBC, Axelar GMP, and other cross-chain messaging protocols, Secret can communicate with almost any blockchain. We're constantly working to integrate new cross-chain technologies.
Low Cost
The only cost involved in utilizing Secret's Confidential Computing Layer is gas for the transaction, which is very low relative to most blockchains. There are no subscription fees or initial integration costs.
Seamless UX
Build your dApp on your preferred blockchain, while Secret handles the confidential computation on the backend. Your users can use their usual wallet, while still benefiting from Secret's capabilities.
Highly Interoperable
Utilizing SecretPath, IBC, Axelar GMP, and other cross-chain messaging protocols, Secret can communicate with almost any blockchain. We're constantly working to integrate new cross-chain technologies.
Low Cost
The only cost involved in utilizing Secret's Confidential Computing Layer is gas for the transaction, which is very low relative to most blockchains. There are no subscription fees or initial integration costs.
Seamless UX
Build your dApp on your preferred blockchain, while Secret handles the confidential computation on the backend. Your users can use their usual wallet, while still benefiting from Secret's capabilities.
Highly Interoperable
Utilizing SecretPath, IBC, Axelar GMP, and other cross-chain messaging protocols, Secret can communicate with almost any blockchain. We're constantly working to integrate new cross-chain technologies.
Low Cost
The only cost involved in utilizing Secret's Confidential Computing Layer is gas for the transaction, which is very low relative to most blockchains. There are no subscription fees or initial integration costs.
Build with Privacy
Get Involved with Secret
Build with Privacy
Get Involved with Secret
Build with Privacy
Get Involved with Secret
Get confidentially computed data
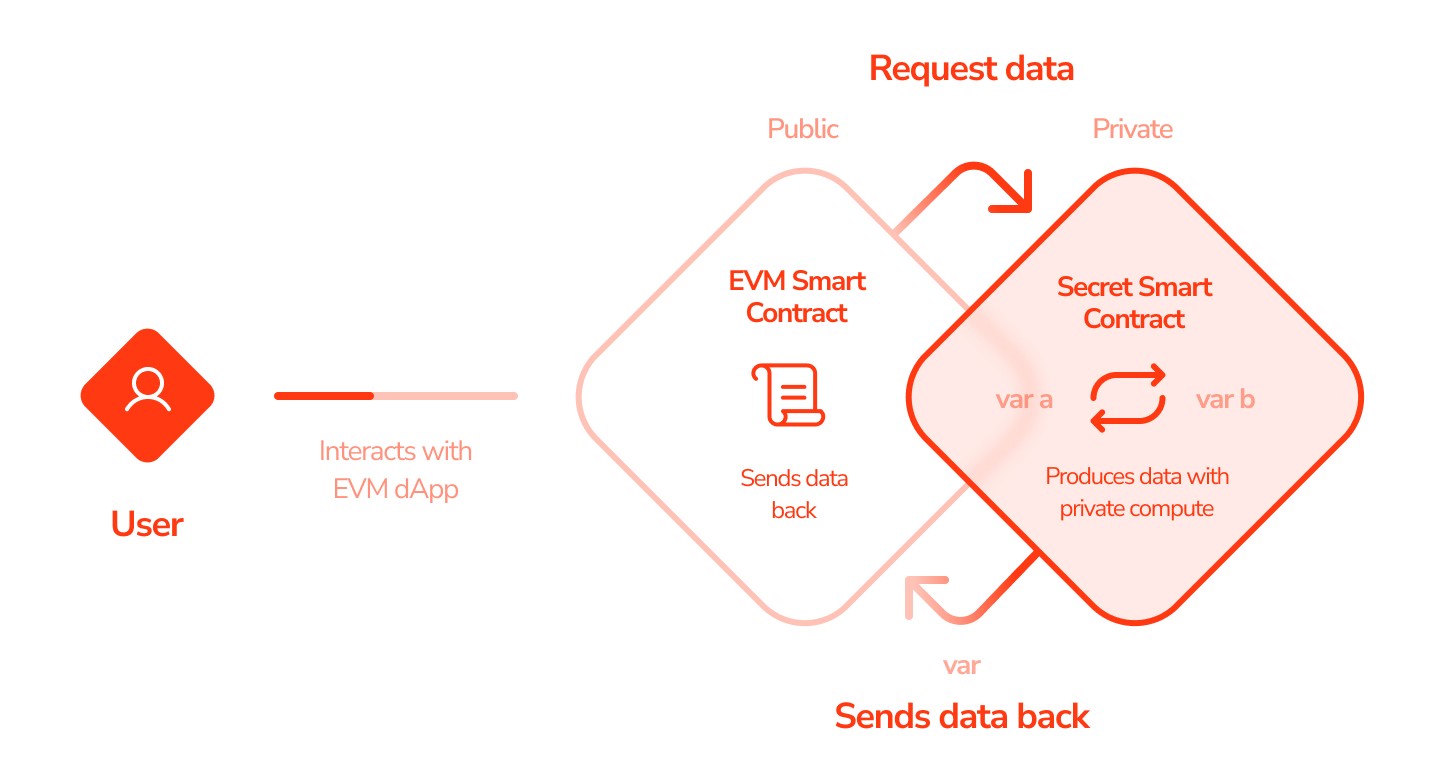
You can ask a Secret smart contract for data that has been confidentially computed without revealing its inputs on-chain. This enables use cases like verifiable on-chain RNG, where the seed used to create a random number is kept hidden.
Get confidentially computed data
You can ask a Secret smart contract for data that has been confidentially computed without revealing its inputs on-chain. This enables use cases like verifiable on-chain RNG, where the seed used to create a random number is kept hidden.

Get confidentially computed data
You can ask a Secret smart contract for data that has been confidentially computed without revealing its inputs on-chain. This enables use cases like verifiable on-chain RNG, where the seed used to create a random number is kept hidden.

Verify encrypted data without revealing it
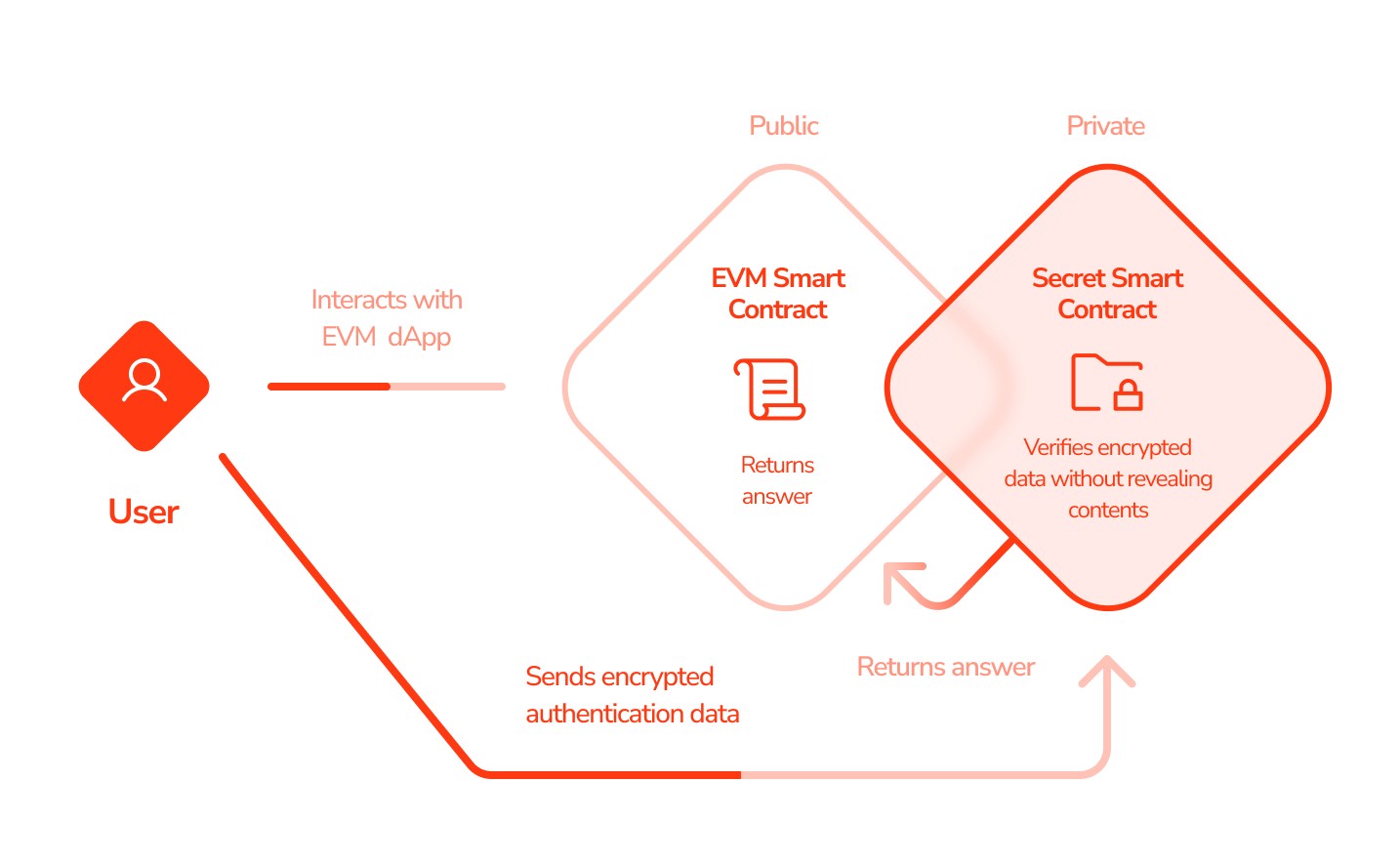
You can send encrypted data to a Secret contract, which can compare it to other data sources, check whether it’s correct, and send back the answer without revealing any sensitive details. This enables you to design tools like secure login functionalities. It can also trigger actions on other chains and process transactions, which allows for use cases like walletless applications.
Verify encrypted data without revealing it
You can send encrypted data to a Secret contract, which can compare it to other data sources, check whether it’s correct, and send back the answer without revealing any sensitive details. This enables you to design tools like secure login functionalities. It can also trigger actions on other chains and process transactions, which allows for use cases like walletless applications.

Verify encrypted data without revealing it
You can send encrypted data to a Secret contract, which can compare it to other data sources, check whether it’s correct, and send back the answer without revealing any sensitive details. This enables you to design tools like secure login functionalities. It can also trigger actions on other chains and process transactions, which allows for use cases like walletless applications.

Create a confidential data layer for your dApp
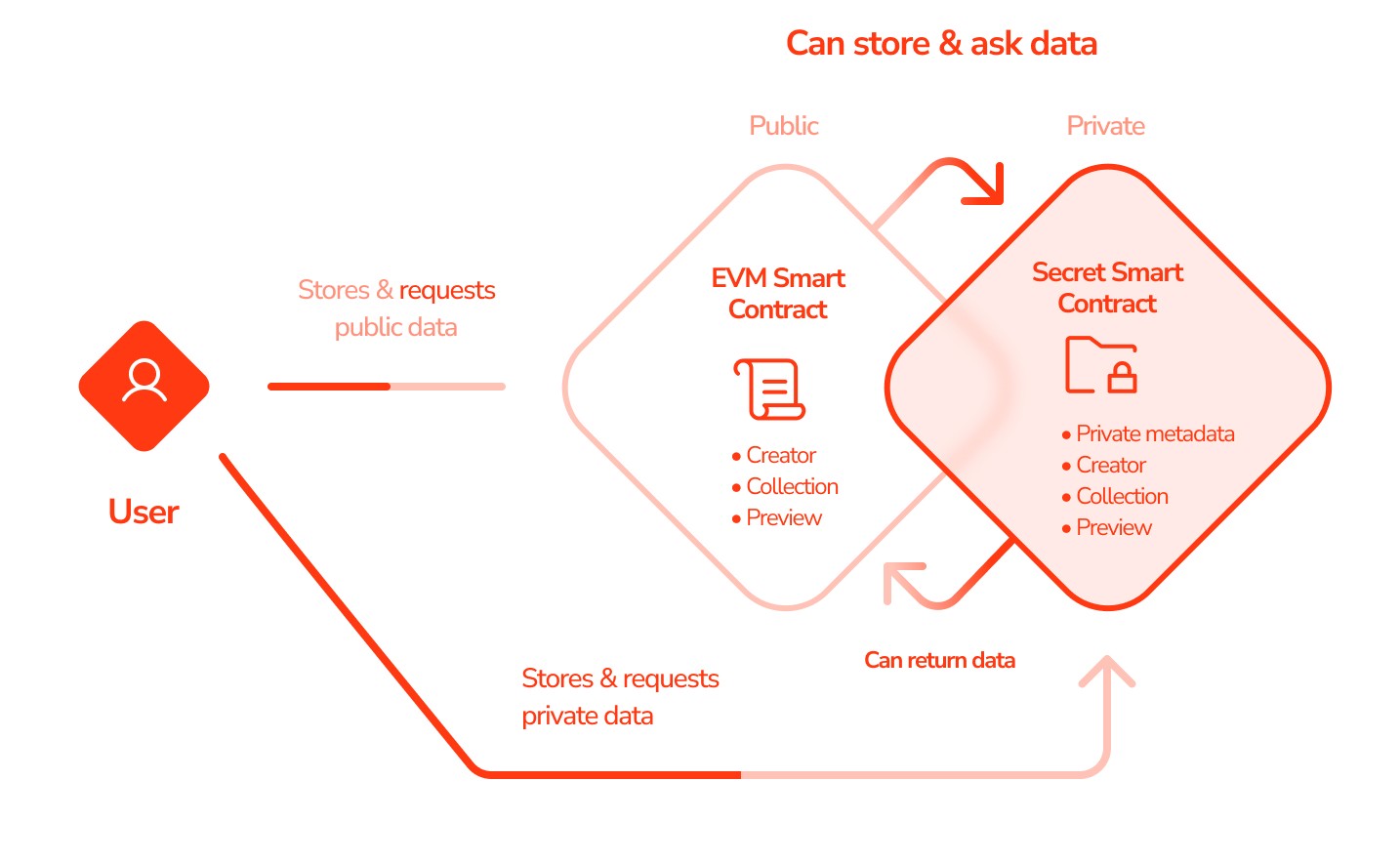
You can host the bulk of your application on your preferred blockchain, while using Secret to handle any confidential data. This allows for features like access control for NFTs, certificates, invoices, and other sensitive documents.
Create a confidential data layer for your dApp
You can host the bulk of your application on your preferred blockchain, while using Secret to handle any confidential data. This allows for features like access control for NFTs, certificates, invoices, and other sensitive documents.

Create a confidential data layer for your dApp
You can host the bulk of your application on your preferred blockchain, while using Secret to handle any confidential data. This allows for features like access control for NFTs, certificates, invoices, and other sensitive documents.



Start building with confidential data
Start building with confidential data
Start building with
confidential data
Our developer documentation makes it easy to integrate Secret’s Confidential Computing Layer into your existing application. Try it out!
Our developer documentation makes it easy to integrate Secret’s Confidential Computing Layer into your existing application. Try it out!
Experience the Future of Privacy
You can host the bulk of your application on your preferred blockchain, while using Secret to handle any confidential data.
Experience the Future of Privacy
You can host the bulk of your application on your preferred blockchain, while using Secret to handle any confidential data.
Experience the Future of Privacy
You can host the bulk of your application on your preferred blockchain, while using Secret to handle any confidential data.











