Share this article
By Ilya Raykker, SCRT Labs Team
At Secret Labs, our mission has always been simple: confidential computing without compromise. Since launching SecretVM, we’ve provided robust, hardware-encrypted environments powered by Intel TDX (Trust Domain Extensions). Today, we are proud to announce a major expansion of our fleet.
SecretVM now supports AMD SEV-SNP, running on high-performance Zen 4 architecture.
This expansion isn't just about adding more cores; it’s about offering our users a choice between two world-class Trusted Execution Environments (TEEs). In this article, we’ll dive deep into the architectural differences, why we believe AMD SEV-SNP meets our rigorous security standards, and share exclusive performance benchmarks from our internal labs.
Read more about AMD SEV-SNP:
Docs: https://www.amd.com/en/developer/sev.html
SNP spec: https://www.amd.com/en/developer/sev.html
The Hardware: Zen 4 vs. Emerald Rapids
To provide a transparent comparison, we deployed two SecretVMs onto our production clusters using the following host specifications. While the guest environments were identical, the host platforms slightly differed:
The Incumbent Standard (Intel) hardware:
CPU: Intel® Xeon® Gold 5515+
Architecture: Emerald Rapids (5th Gen)
TEE: Intel® TDX (Trust Domain Extensions)
RAM: 256 GB ECC 4800 MHz
Disks: 2×960 GB SSD NVMe Soft RAID
The New Challenger (AMD) hardware:
CPU: AMD EPYC™ 9124 16-Core Processor
Architecture: Zen 4 (Genoa)
TEE: AMD SEV-SNP (Secure Encrypted Virtualization with Secure Nested Paging)
RAM: 128 GB ECC 4800 MHz
Disks: 2×960 GB SSD NVMe Soft RAID
Deep Dive: AMD SEV-SNP vs. Intel TDX
While both technologies aim to solve the same problem—protecting data in use from a malicious hypervisor or cloud provider—they take different paths to get there.
1. The Trust Boundary (TCB)
Intel TDX is designed with a minimal Trusted Computing Base. It utilizes a specialized CPU mode called SEAM (Secure Arbitration Mode) and the TDX Module to strictly isolate the "Trust Domain" from the rest of the system.
AMD SEV-SNP relies on the AMD Secure Processor (PSP), a dedicated security co-processor embedded in the die. While this historically created a slightly larger TCB (including some guest firmware), the introduction of SNP (Secure Nested Paging) has closed critical integrity gaps, preventing the hypervisor from remapping memory or replaying old data.
Architecturally, Intel TDX offers a more streamlined TCB option here due to its smaller attack surface (Minimal TCB). A smaller TCB means fewer components to trust and fewer potential vulnerabilities. AMD SEV-SNP has a larger TCB (historically considered "worse"), but its rigorous hardware-enforced integrity checks have effectively neutralized this disadvantage for practical enterprise security.
2. Encryption Standards
This is the most common point of comparison.
Intel TDX uses AES-256-XTS via Multi-Key Total Memory Encryption (MKTME).
AMD SEV-SNP typically utilizes AES-128-XTS for memory encryption.
Theoretically, AES-256 offers a higher margin of safety against future quantum attacks. However, in the context of current computing, AES-128 remains computationally unbreakable. For 99% of enterprise use cases, the practical security difference is negligible compared to the operational stability AMD provides.
Additional considerations
AMD SEV-SNP is an established Confidential Computing platform. AMD has been iterating on SEV since the EPYC Naples generation. SEV-SNP is the third major iteration, meaning the drivers, kernel support, and tooling are incredibly battle-tested.
While our initial offering runs on Zen 4, the architecture paves the way for Zen 5, which introduces even more robust side-channel mitigations (including mitigations for the RDSEED entropy bug) and trusted I/O enhancements, making the platform future-proof.
Lab Benchmarks
We put our AMD EPYC 9124 against our optimized Intel TDX environment (Xeon Gold 5515+). The results were surprising: AMD is the king of raw compute, while Intel reigns over I/O.
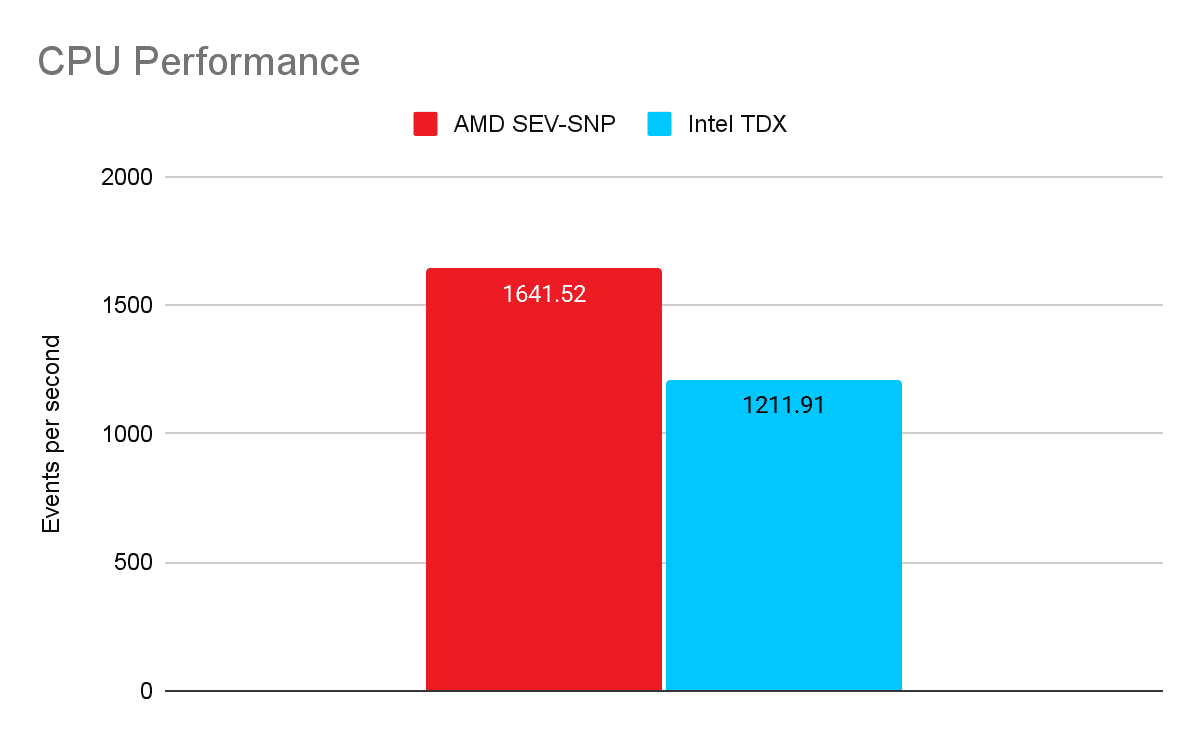
1. CPU Performance (Prime Number Calculation)
Benchmark: Sysbench
AMD's Zen 4 core architecture demonstrates superior raw instruction throughput in this test, processing ~35% more events per second than the Intel environment.
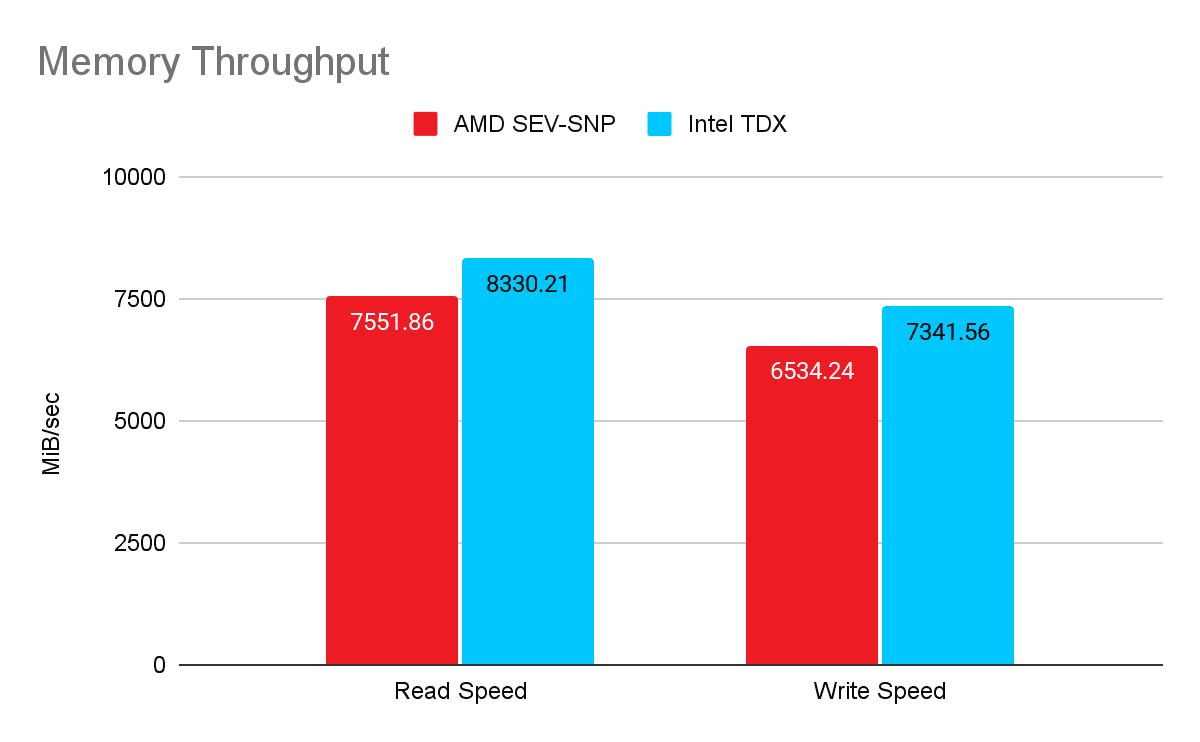
2. Memory Throughput
Benchmark: Sysbench
Intel's TDX architecture, likely benefiting from MKTME optimizations, showed higher sustained bandwidth.
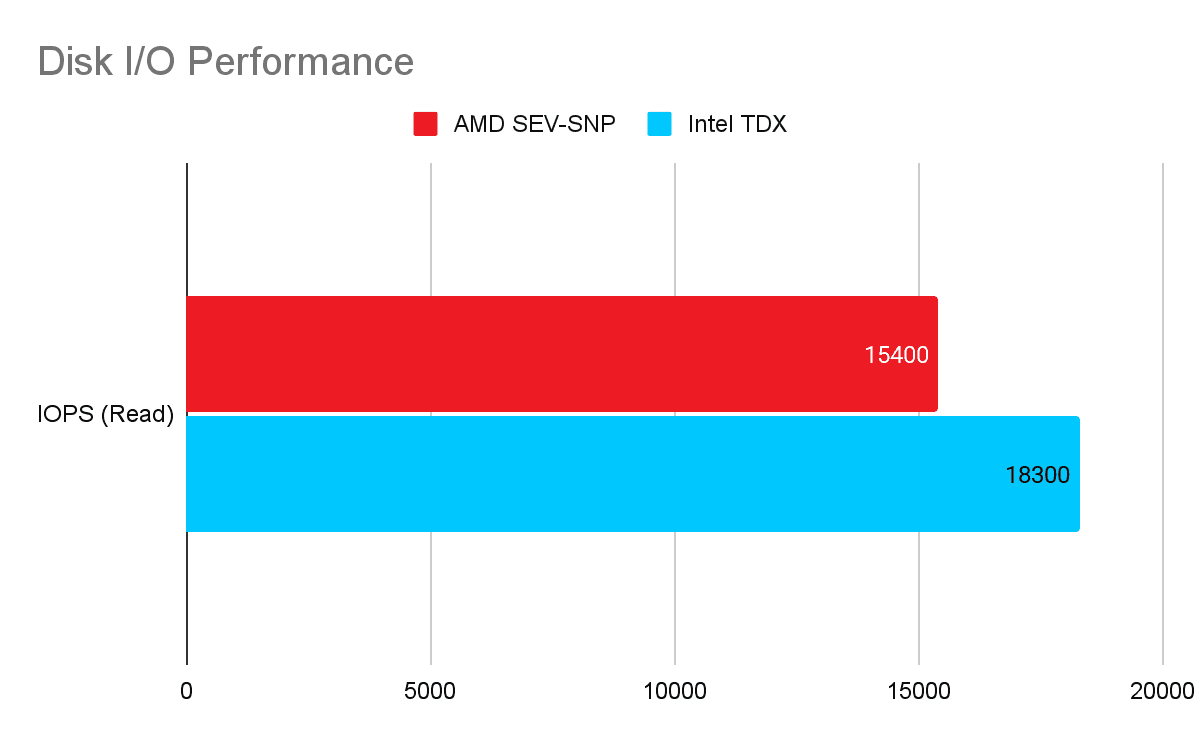
3. Disk I/O Performance
Benchmark: FIO
The most distinct difference appeared in storage I/O. The Intel TDX environment handled high-frequency I/O operations more efficiently, likely due to lower overhead in the virtualization exit path for storage interrupts. While guest resources were strictly equal across both environments, the Intel environment benefited from Emerald Rapids' optimized virtualization exit paths and a larger host-level page cache (supported by the 256 GB RAM configuration). This combination reduces the latency of storage interrupts, making it the more responsive choice for intensive read/write cycles.
Conclusion: Which SecretVM Should You Choose?
With the addition of AMD SEV-SNP, you now have the power to optimize based on your specific workload:
Choose AMD SEV-SNP if your workload is CPU-heavy. Tasks like batch processing, cryptographic calculations, and heavy compile jobs will fly on the Zen 4 cores.
Choose Intel TDX if your application is Data-intensive. High-frequency trading, large in-memory databases, and I/O-bound microservices will benefit from the superior memory and disk throughput.
Both platforms offer the hardware-grade isolation that Secret Labs guarantees and both are available at the SecretAI portal. Welcome to the new era of choice in confidential computing.
As we add more hardware options, the performance of both Intel TDX and AMD SEV-SNP-based SecretVMs may vary.
